Sensitive information breaches
A company called Orthus decided to share with me the results of 100,000 hours of spying on users in different organisations. The statistics were a by-product of the company’s service which …
A company called Orthus decided to share with me the results of 100,000 hours of spying on users in different organisations. The statistics were a by-product of the company’s service which looks for leakages of sensitive data. Some of its clients use the information to educate users, others use it to nail miscreants.
Most of the spying was conducted last year, so this year’s results are likely to be different but the underlying conclusions from the results are unlikely to change much.
As I was reading the report, I imagined technical information security measures as a low circular wall. Inside are all the users and the data. All they have to do to defeat the security is to grab the information and either throw it over the wall, or hop over with it themselves.
The report talks about the vectors along which your sensitive data will find its way to the outside world. And, by heck, there’s a lot of them. Last year it was printers, PDAs, MP3 players, USB flash drives, instant messaging (IM), Skype, Facebook, Bluetooth, Wireless and Infrared. Next year it will be different as the company closes old vectors and new ones appear. It’s best to imagine information security as a balloon – you can squeeze one part, but another part will instantly expand.
It’s not necessarily that the users are malicious. They are frequently driven by the need to get work done quickly or conveniently. They might want to get something important on to their laptops to work on at the weekend and, if conventional routes are blocked, they’ll find another one.
Apart from the ‘traditional’ leakage methods of file copying, removable media and corporate email, the three communications applications most likely to carry sensitive information were web mail, instant messaging and social networking websites.
These days, it will often be an online (Web 2.0) service which promises secure data transfer. But what happens at the other end? Does it sit on the remote server unencrypted? Once you’ve downloaded it at home and deleted the online version, does it really disappear or is it part of some humungous database in the sky?
By now, it’s becoming clear that the main issue is a human one. In fact, the report states that, “trusted authorised users are most likely to be the source of information leaks.” You can, and should, throw technologies at securing your information but, in the end, it’s mainly the insiders who are the causes of leaks.
The Orthus report highlights the customer service and IT departments as the most likely sources of leaks. And, furthermore, laptop and notebook computers, were twice as likely to be associated with a leakage event than a desktop computer. The company speculates that this may be something to do with the fact that users treat notebooks more as personal devices. (If true, this does not bode well for the explosion of PDA devices such as the BlackBerry and iPhone that is currently taking place.)
Finally, you might be interested to know that, when it comes to time of day for breaches, 81 percent is during the extended working day of 7am to 7pm but the incidents between 7pm and 6am were all classified as ‘High Severity’.
Never mind all the headline-grabbing stuff about cyber criminals, how certain are you that your own users are handling your information safely? Orthus will happily check you out. But, with the above warnings, I suspect it’s done more than enough to alert you to the issues.
Share & Comment
Related Posts
SME News
- Entrepreneurs 2012 with President Bill Clinton 13-16 November
- IDCEE 2012. Internet Technologies and Innovations
- Nurturing the next generation of social entrepreneurs
- Get Britain Trading needs you
- Manufacturing gains, but economy fragile
- Minister to answer webcast questions on apprenticeships
- Staff beat £230 million a day cost of big freeze
 SME Blog
SME Blog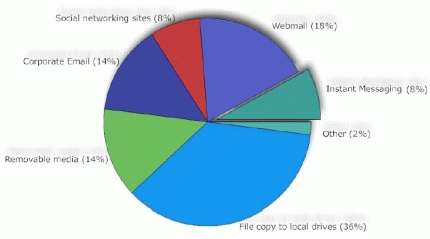

 0 comments
0 comments











Commenting Is Easy
Do you agree with this blog post? Disagree? Have something to add that others might find helpful? Then please leave a comment in the box below.
If you'd like to have your image included next to your comments here, then you can set yourself up with an avatar in just a couple of clicks.